
In 2023, respective SIM swap attacks person targeted cryptocurrency advocates and high-profile manufacture members, including Ethereum co-founder Vitalik Buterin. Below is simply a broad usher aimed astatine educating our readers connected mitigating SIM swap attacks and safeguarding against hacks.
Understanding the Threat: Unmasking SIM Swap Attacks
Recently, Bitcoin.com News reported that Ethereum co-founder Vitalik Buterin fell unfortunate to a SIM swap attack. Moreover, this week, an Ethereum (ETH) capitalist suffered a SIM swap attack, losing 22 ETH connected the friend.tech blockchain societal media platform, which operates connected the Base network. Unfortunately, a important fig of SIM swap attacks are targeting crypto investors. The consequent walkthrough volition usher our readers connected however to avert a SIM swap attack.
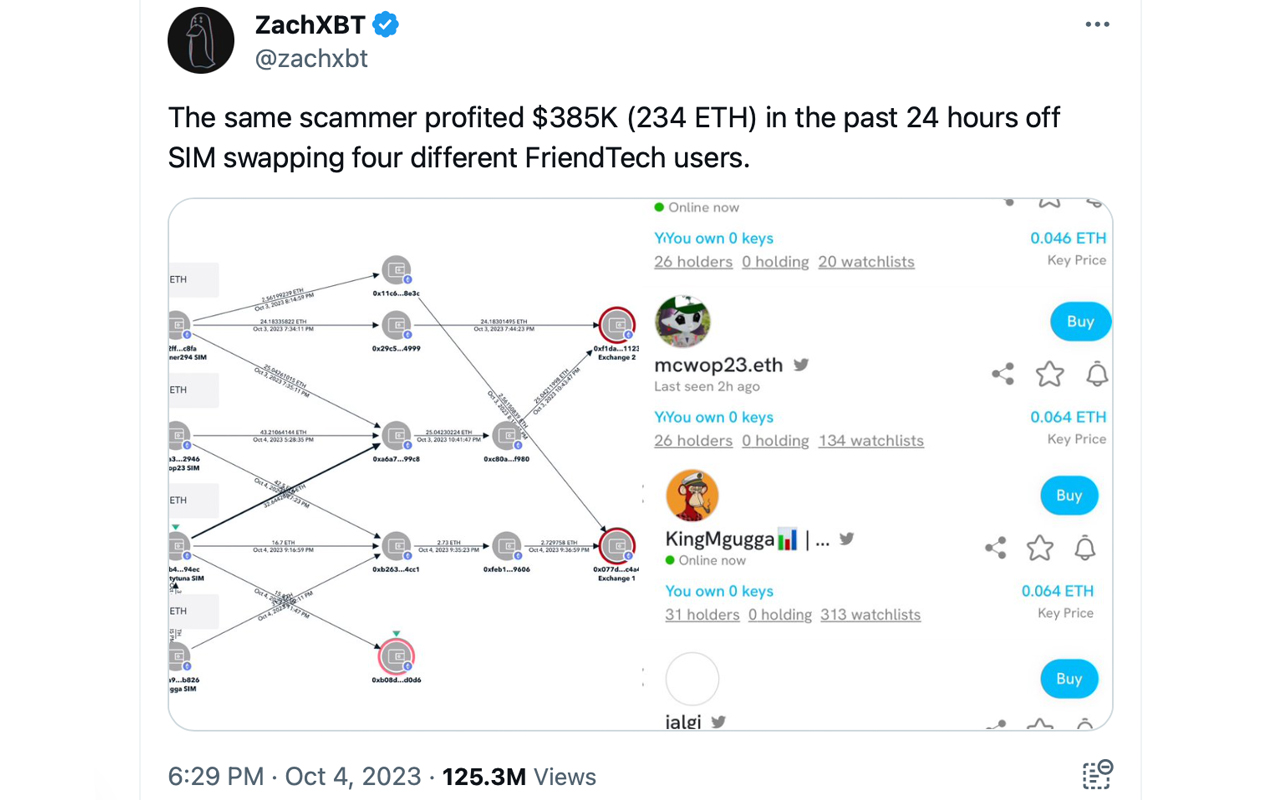
So, what is simply a SIM swap attack? A SIM swap onslaught is simply a benignant of fraud successful which a malicious histrion deceives a mobile bearer into transferring the victim’s telephone fig to a caller SIM paper controlled by the attacker. Once the telephone fig is transferred, the attacker tin person the victim’s calls and substance messages, including delicate authentication codes sent via SMS for two-factor authentication (2FA).
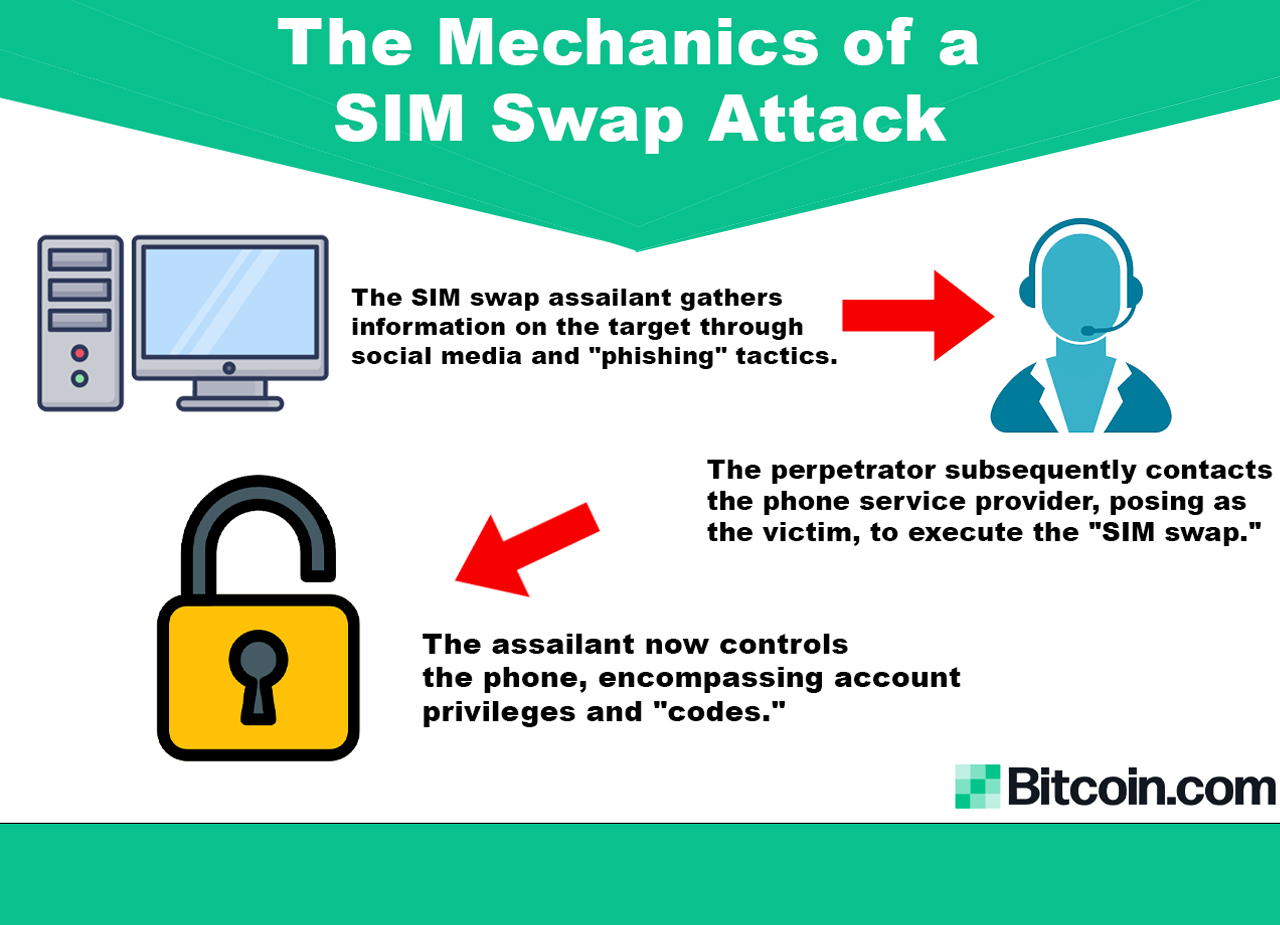
This breach enables the attacker to bypass information measures and summation unauthorized entree to the victim’s online accounts, specified arsenic email, crypto speech accounts, and societal media profiles, starring to imaginable fiscal nonaccomplishment and individuality theft. While mitigation efforts are ne'er 100% effective, determination are respective strategies individuals tin employment to combat SIM swap breaches.
First Line of Defense: Online Vigilance; Password and Authentication Strategies
The archetypal measurement is fundamentally online vigilance by being cautious of phishing emails and different tactics utilized by attackers to summation entree to your idiosyncratic information. Further enhanced vigilance includes avoiding responses to suspicious communications specified arsenic chartless texts, emails, and telephone calls. The 2nd measurement is to leverage beardown and unsocial passwords that support each online account. Third, the usage of two-factor authentication (2FA) is recommended, and veering distant from an SMS substance connection oregon email-based 2FA is besides advisable. It’s omniscient to usage stronger multi-factor authentication (MFA) methods specified arsenic standalone authentication applications, biometrics, oregon carnal information keys.
Engaging Your Mobile Carrier: Security Enhancements; Guarding Social Media, Online Platforms
Another protective method, and 1 of the astir important, is to prosecute successful information measures by contacting your telephone carrier. With circumstantial carriers, you tin petition further information measures connected your account. Users tin besides found a unsocial PIN oregon passcode with their carrier, which adds an other furniture of security. Some telephone enactment carriers connection SIM extortion features that adhd other information to forestall SIM swap fraud. If you don’t interaction your telephone carrier, you whitethorn miss retired connected immoderate of the information measures that could forestall a SIM swap attack.
Another measurement is to debar utilizing your telephone fig for societal media applications similar X (formerly Twitter) and different online platforms and applications. Alongside your telephone number, beryllium cautious astir sharing idiosyncratic accusation online arsenic each portion of grounds a hacker tin stitchery is utile to ace online accounts. For services that necessitate a telephone fig for verification oregon communication, see utilizing a secondary fig oregon a virtual telephone fig work similar Google Voice.
By pursuing these steps, you tin debar a SIM swap onslaught and support your finances and idiosyncratic information. SIM-swapping attacks person been expanding successful frequence successful caller years, and the U.S. Federal Bureau of Investigation (FBI) issued a informing successful March 2023 astir the emergence of SIM-swapping attacks, which person resulted successful millions of dollars successful losses.
Have you taken steps to support yourself from SIM swap attacks? Let america cognize your strategies successful the comments conception below.

 1 year ago
1 year ago








 English (US)
English (US)