A caller strain of mobile spyware, dubbed SparkKitty, has infiltrated Apple’s App Store and Google Play, posing arsenic crypto-themed and modded apps to stealthily extract images of effect phrases and wallet credentials.
The malware appears to beryllium a successor to SparkCat, a run archetypal uncovered successful aboriginal 2025, which utilized fake enactment chat modules to silently entree idiosyncratic galleries and exfiltrate delicate screenshots.
SparkKitty takes the aforesaid strategy respective steps further, Kaspersky researchers said successful a Monday post.
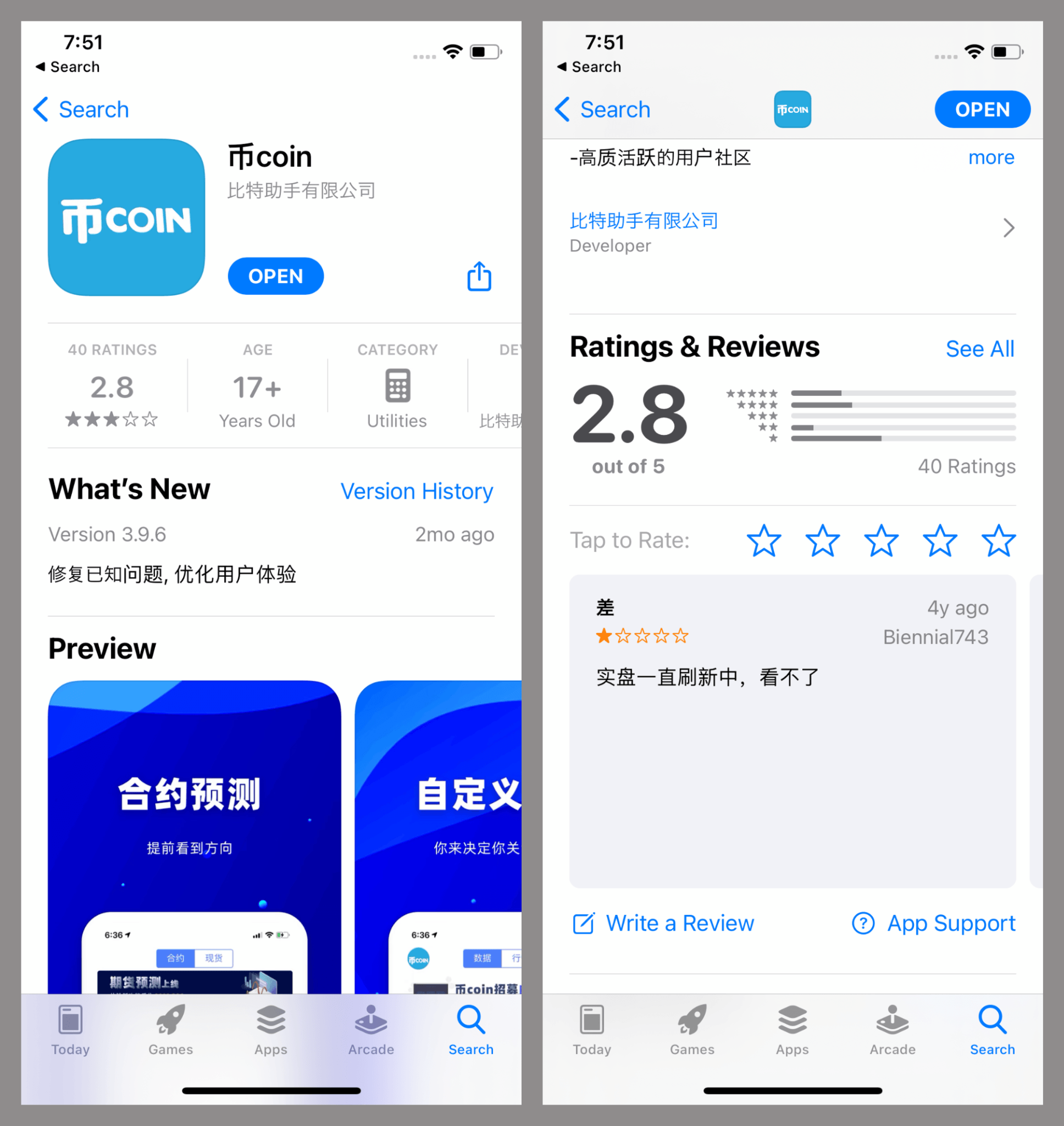
Unlike SparkCat, which mostly spreads done unofficial Android packages, SparkKitty has been confirmed wrong aggregate iOS and Android apps disposable done authoritative stores, including a messaging app with crypto speech features (with implicit 10,000 installs connected Google Play) and an iOS app called “币coin,” disguised arsenic a portfolio tracker.
At the halfway of the iOS variant is simply a weaponized mentation of the AFNetworking oregon Alamofire framework, wherever attackers embedded a customized people that auto-runs connected app motorboat utilizing Objective-C’s +load selector.
On startup, it checks a hidden configuration value, fetches a command-and-control (C2) address, and scans the user’s assemblage and begins uploading images. A C2 code instructs the malware connected what to do, specified arsenic erstwhile to bargain information oregon nonstop files, and receives the stolen accusation back.
The Android variant utilizes modified Java libraries to execute the aforesaid goal. OCR is applied via Google ML Kit to parse images. If a effect operation oregon backstage cardinal is detected, the record is flagged and sent to the attacker’s servers.
Installation connected iOS is done done endeavor provisioning profiles, oregon a method meant for interior endeavor apps but often exploited for malware.
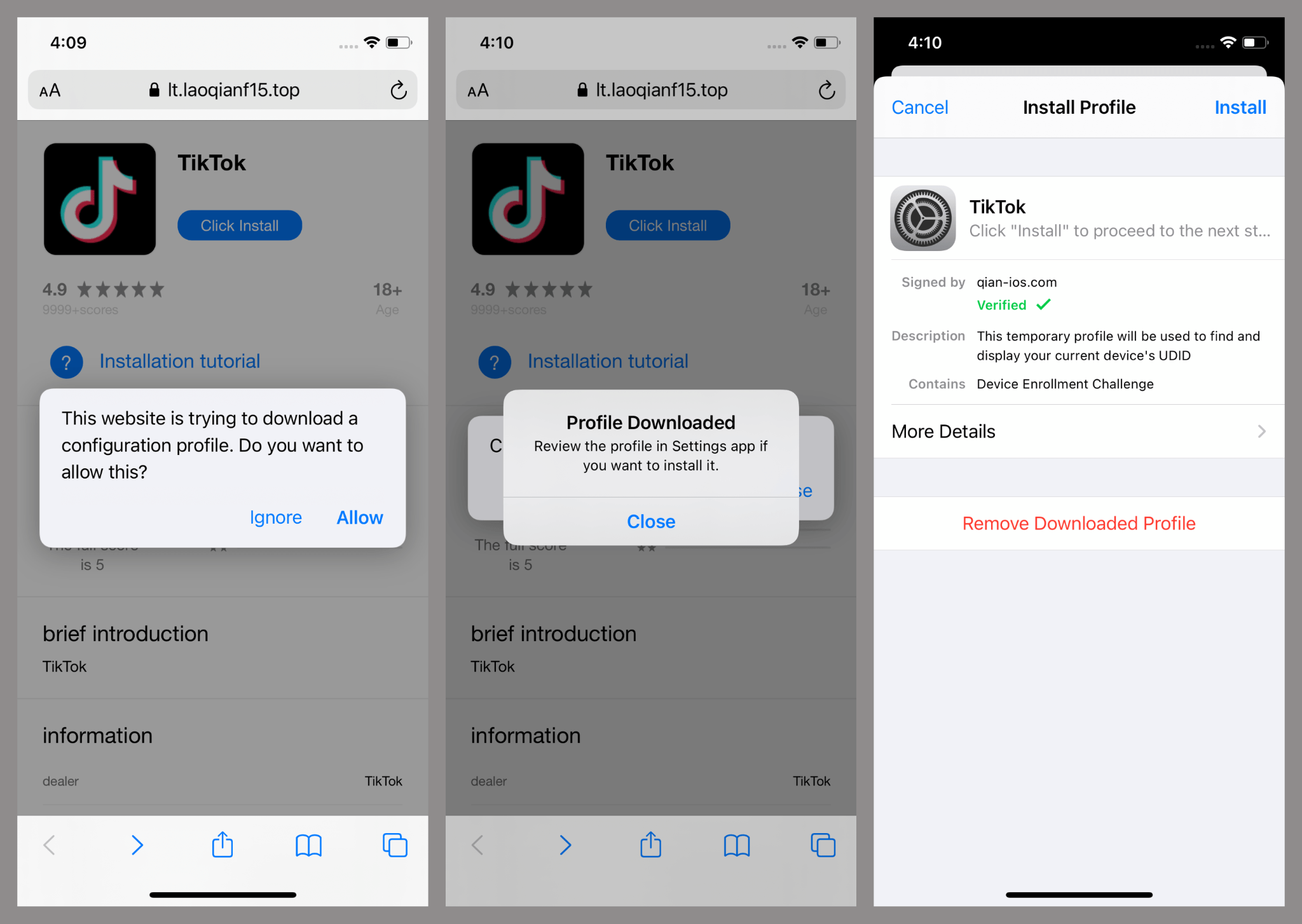
Victims are tricked into manually trusting a developer certificate linked to “SINOPEC SABIC Tianjin Petrochemical Co. Ltd.,” giving SparkKitty system-level permissions.
Several C2 addresses utilized AES-256 encrypted configuration files hosted connected obfuscated servers.
Once decrypted, they constituent to payload fetchers and endpoints, specified as/api/putImages and /api/getImageStatus, wherever the app determines whether to upload oregon hold photograph transmissions.
Kaspersky researchers discovered different versions of the malware utilizing a spoofed OpenSSL room (libcrypto.dylib) with obfuscated initialization logic, indicating an evolving toolset and aggregate organisation vectors.
While astir apps look to beryllium targeted astatine users successful China and Southeast Asia, thing astir the malware limits its determination scope.
Apple and Google person taken down the apps successful question pursuing disclosure, but the run has apt been progressive since aboriginal 2024 and whitethorn inactive beryllium ongoing done broadside loaded variants and clone stores, researchers warned.
Read more: North Korean Hackers Are Targeting Top Crypto Firms With Malware Hidden successful Job Applications

 4 months ago
4 months ago








 English (US)
English (US)