The contention for WEB3 has begun. Venture capitalists, cryptocurrency startups, engineers, and visionaries are processing WEB3 (or Web 3.0) powered by blockchain. A caller frontier arose, much democratic, decentralized, independent, and perfect for information recovery.
But is everything truthful cleanable regarding decentralization and information of infrastructures? No, and galore cases of man-in-the-middle attacks are impervious of that.
But to lick the information issue, let’s retrieve what WEB3 is. The halfway conception of WEB3 is to lick the information problems caused by centralization and to supply radical with authorization implicit their information and identification. So astatine what level of exertion are these unfortunate incidents of information breaches occurring successful your blockchain infrastructure? Let’s fig it out.
To absorption connected the interior aspects of WEB3, technologies specified arsenic EVM, Solidity, and JavaScript inactive play a monolithic role. However, we usage Node providers and WEB3 API providers erstwhile discussing backend features.
Node providers are companies that let you to usage their services alternatively of moving your nodes. This is precise convenient due to the fact that alternatively of mounting up your node and experiencing each the accent and disbursal that comes with it, you tin nonstop your dApp transaction requests implicit the Internet to the node provider. If you’re funny successful astute declaration development, you whitethorn usage 1 oregon 2 node providers (for redundancy).
There are many WEB3 API providers; however, successful galore instances, these companies enactment with nodes down the scenes. With these tools applied, you tin get immoderate pre-compiled and pre-computed information connected the chain.
Moreover, it is elemental to found reliable connection and enactment betwixt antithetic applications done these WEB3 APIs. In addition, prime APIs support coding accordant and stable. We, therefore, trust connected trustworthy WEB3 APIs the astir erstwhile creating applications.
 Difference betwixt Node providers and WEB3 API providers: WEB3 supplier allows your exertion to pass with a blockchain node by submitting JSON-RPC requests to a server. Node work providers tally distributed node clients down the scenes and fto them constitute to and work from a blockchain utilizing an API key.
Difference betwixt Node providers and WEB3 API providers: WEB3 supplier allows your exertion to pass with a blockchain node by submitting JSON-RPC requests to a server. Node work providers tally distributed node clients down the scenes and fto them constitute to and work from a blockchain utilizing an API key.
What is the information menace for dApps developers?
Nodes are inactive comparatively primitive technologies, but they are inactive valuable. For example, a WEB3 node cannot archer you what users person deposited successful their accounts. Besides simply providing earthy blockchain information, nodes cannot process aggregate astute contracts. Furthermore, nodes person constricted capabilities and tin lone process 1 chain. Fortunately, determination are APIs disposable to assistance you circumvent this limitation.
APIs specify and standardize applications’ interactions, allowing you to usage earthy blockchain data. This is wherefore WEB3 APIs are adjuvant for dApp development. WEB3 APIs are a cardinal constituent successful the improvement of dApps; successful summation to offering a elemental interface, they let a portion of bundle to interact with different applications. Because reliable APIs let for accordant coding successful a unchangeable environment, dApp developers don’t request to reinvent the wheel.
Furthermore, by utilizing these WEB3 supplier APIs, you tin easy nexus to nodes. Therefore, you bash not person to interest astir connecting to nodes erstwhile utilizing these APIs. When interacting with these providers, you whitethorn besides person each sorts of invaluable precalculated and precompiled on-chain data.
But specified services bash not wholly adjacent developers’ requests successful the information plans, and successful astir cases, you person to wage successful beforehand for their use.
The information is that determination are much and much cases of dApps being hacked utilizing the man-in-the-middle onslaught we mentioned above.
This is erstwhile an attacker, utilizing vulnerabilities successful DNS servers (for example), switched servers to service jsonrpc-endpoints traffic.
One unfortunate is known to have mislaid 16.5 WBTC (~$350,840). And astir 23 cryptocurrency projects person already encountered a akin DNS attack.
A precise elemental solution allows you to support yourself from specified man-in-the-middle attacks. And we volition instrumentality to this.
Also, if you person a improvement team, you tin spell your ain mode and effort to physique your solution, but you request a super-skilled squad of like-minded radical to marque it work.
The trouble of this process is that you tin importantly overestimate your strength. A task that seems casual past raises galore questions, which are solved by galore years of acquisition successful one’s work. Therefore, if you person a batch of clip and resources, you should judge this path.
Violation of 3 main blockchain principles successful the WEB3
So let’s instrumentality a enactment present and look astatine the existent information challenges successful the WEB3 satellite from an infrastructure perspective.
The main principles of blockchain are
- decentralization
- transparency
- trustlessness
But does it enactment successful practice? Take a look astatine the most fashionable dApp architecture.
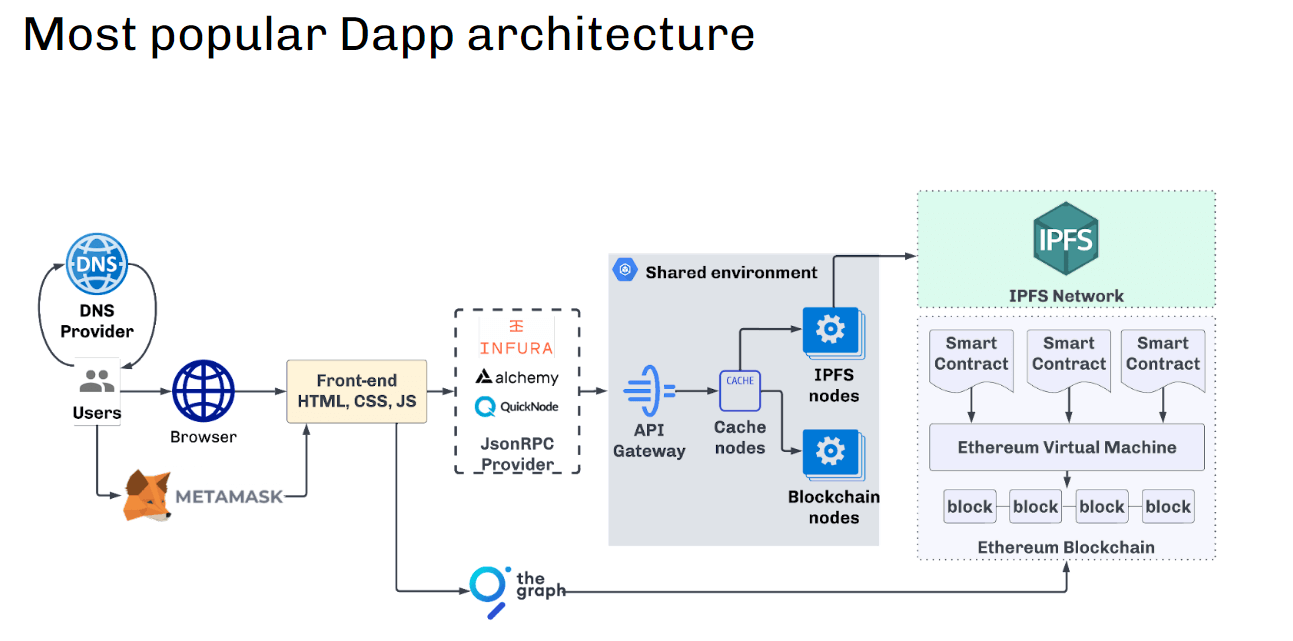 Most fashionable dApp architecture
Most fashionable dApp architecture We tin spot that users connected the beforehand extremity are sending requests to JSON-RPC providers (this could beryllium Infura, Alchemy, Quicknode, etc.).
We tin spot that users connected the beforehand extremity are sending requests to JSON-RPC providers (this could beryllium Infura, Alchemy, Quicknode, etc.).
So the requests are routed to a shared situation wherever we person nary power implicit the information translation astatine the API gateway, caching engine, blockchain nodes, oregon thing else.
And this is wherever the archetypal occupation arises due to the fact that a shared situation means that galore users, bots, and hackers, successful particular, enactment successful the aforesaid environment. This is simply a existent achromatic container for the developer that attracts excessively overmuch attraction from attackers.
Well, this attack contradicts each 3 principles of WEB3 because:
- It centralizes entree to the Blockchain, passing everything done a shared environment;
- It is not transparent—we cannot verify responses from specified an API;
- Therefore, it cannot beryllium called existent mistrust since the information issues of specified an infrastructure are based simply connected trust. See for yourself successful the pursuing diagram.
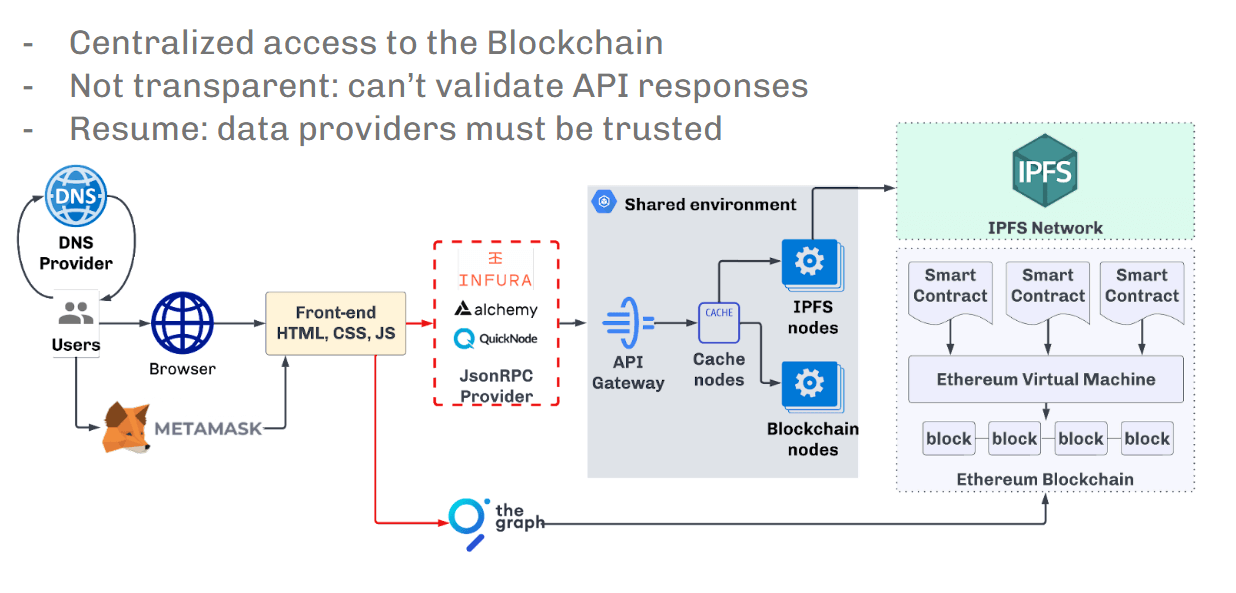 dApp architecture issues
dApp architecture issues The 2nd contented is that the described infrastructure version allows for man-in-the-middle attacks, which criminals periodically use.
The 2nd contented is that the described infrastructure version allows for man-in-the-middle attacks, which criminals periodically use.
The pursuing services tin beryllium attacked:
-
- Domain oregon DNS registrars
- JSON-RPC providers
- Any third-party aggregated services
A self-hosted clump of blockchain nodes is the lone solution
But is determination a solution? Yes — configured on-prem environment.
First, it uses a self-hosted clump of blockchain nodes. All nodes are initialized from authoritative genesis and synchronized utilizing p2p. This ensures information consistency.
Nodes should beryllium updated periodically with reduced snapshots to tally arsenic efficiently arsenic possible. The perfect solution is automatically creating caller nodes from the reduced snapshot erstwhile zooming. If you initialize the node from scratch, this attack allows you to get a caller node wrong 30 minutes alternatively of respective days.
Another captious constituent is the automatic update of the blockchain bundle aft its release—this tin besides beryllium done. The main happening is to make a snapshot with the caller mentation (as sometimes it whitethorn necessitate immoderate information operations, which tin instrumentality time), and past the caller nodes should commencement automatically with the caller snapshot and updated software.
Below is an infrastructure diagram that solves astir of the described problems.
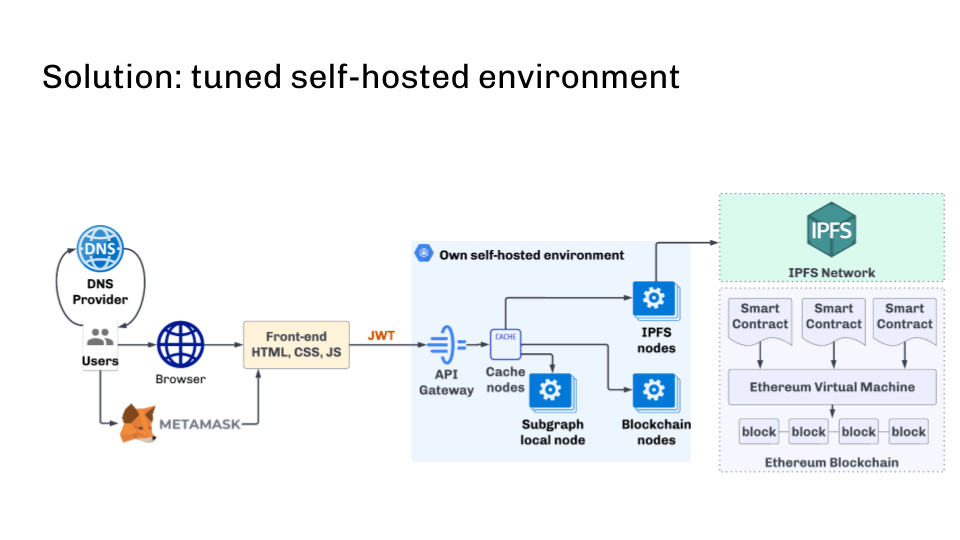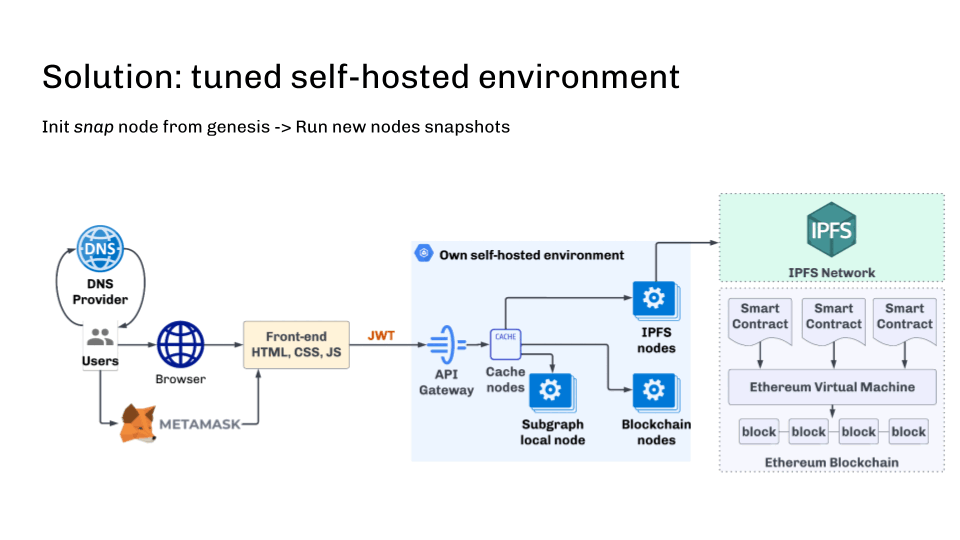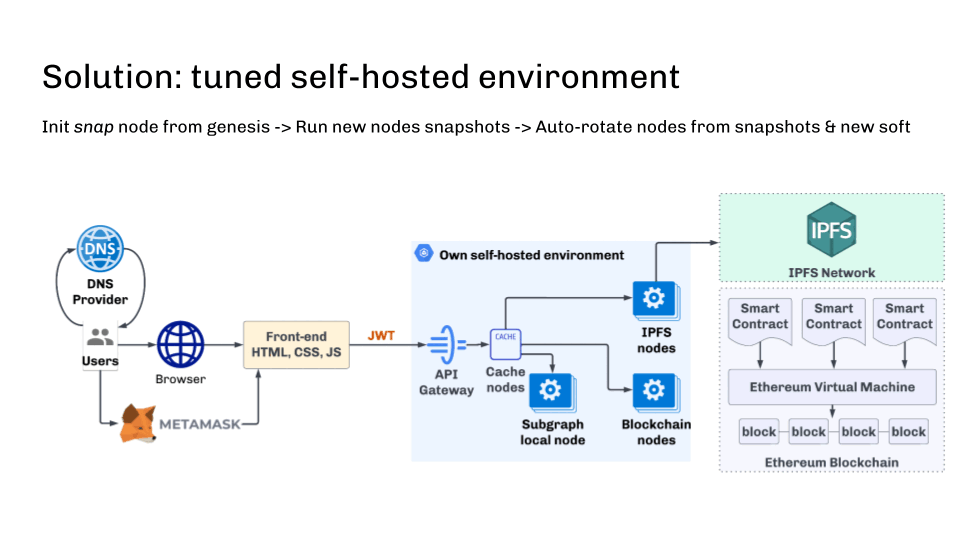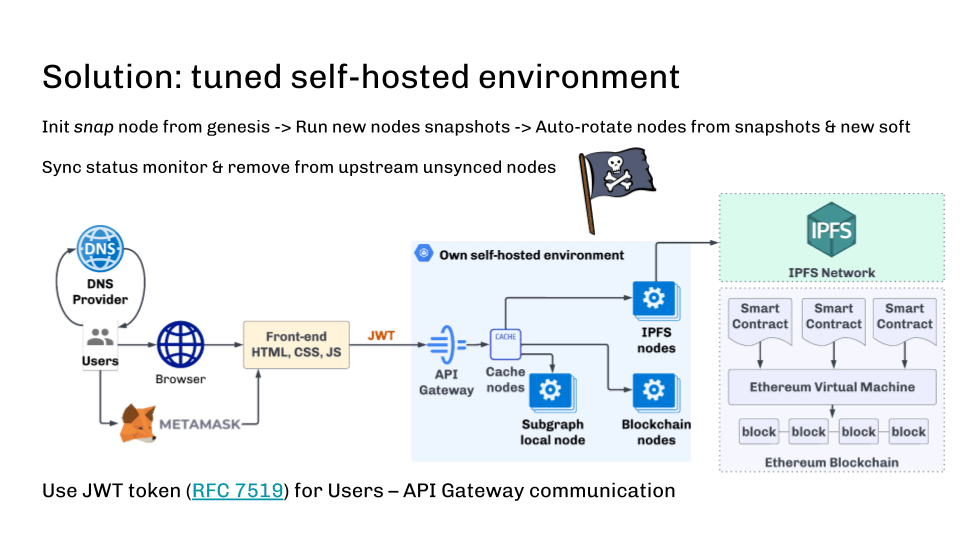 dApp infrastructure solution
dApp infrastructure solutionIt is besides important to show the synchronization authorities and exclude those nodes that are down the upstream flow. This tin beryllium done, for example, with the assistance of wellness checks.
In summation to the information that entree tin beryllium constricted by IP address, it is worthy mentioning that the bully aged JWT token tin support against domain registrar oregon DNS attacks. JWT token is easy integrated into web3js and different libraries and should beryllium implemented connected the API gateway broadside successful our blockchain cluster.
In this way, we marque the blockchain endpoint unafraid and decentralized.
Summing up
Web3 is inactive successful its aboriginal stages. But the contention for decentralization is already on. And you volition beryllium capable to spot that the astir unafraid applications are apt to beryllium the ones that usage the astir innovative and open-source approaches.
And therefore, you should not disregard the basal principles of WEB3 due to the fact that past your recently created dApp volition not supply information to different participants. The lone enactment presently disposable is an autonomous cluster of geo-distributed blockchain nodes.
Author:
Daniel Yavorovych
Co-Founder & CTO at RPCFast and Dysnix
The station How to lick the blockchain infrastructure information occupation portion creating a dApp appeared archetypal connected CryptoSlate.

 2 years ago
2 years ago






 English (US)
English (US)