On Wednesday, a hacker managed to bargain 80,000 ether (ETH) retired of Solana done the Solana-Ethereum span Wormhole. Here’s however the hacker pulled it off.

One of the worst hacks against the Solana blockchain happened connected Wednesday erstwhile a hacker managed to transportation 80,000 ether (ETH), implicit $214 cardinal astatine the infinitesimal of writing, retired of the Solana strategy and into the Ethereum blockchain done the Wormhole span – a work providing the quality to transportation funds betwixt the antithetic blockchains.
Explained successful a tweet thread by the pseudonymous Twitter illustration smartcontracts, the hacker finalized the exploit by transferring the 80,000 ETH retired of the Wormhole astute declaration connected Ethereum successful a azygous transaction. As it turned out, this was conscionable the last determination successful a bid of hacks that enabled the hacker to bargain the funds.
“Although it’s dramatic, this transaction is conscionable the precise extremity of an absorbing bid of events. I had to commencement moving my mode backward to fig retired however this was adjacent possible,” smartcontracts tweets.
Guardians signed disconnected a mendacious transfer
Wormhole is simply a alleged bridge, a smart contract, connected Ethereum successful this case, that provides a mode to determination crypto assets betwixt antithetic blockchains. According to smartcontracts, from a high-level viewpoint, Wormhole specifically has a acceptable of co-called guardians that motion disconnected connected transfers betwixt the blockchains.
The Wormhole guardians had someway signed disconnected connected this 80,000 ETH transportation arsenic if it was 100% legitimate.
“The transaction that pulled retired 80,000 ETH was really the attacker transferring 80,000 ETH from Solana to Ethereum. I primitively thought that the declaration mightiness person incorrectly validated the signatures connected the transfer, but the signatures [were] wholly checked out.”
According to smartcontracts, the archetypal breakthrough and partial mentation came from a transaction connected Solana which someway minted 120,000 “Wormhole ETH”, wrapped ether connected Solana, retired of nowhere. Since the hacker was capable to mint Wormhole ETH connected Solana, helium was capable to correctly retreat it backmost to Ethereum.
“Solana is kinda weird”
Examining the hacker’s transaction history, there’s a transaction that came close earlier the minting of the 120,000 Wormhole ETH. In this transaction, the hacker mints lone 0.1 Wormhole ETH, arsenic if the hacker was investigating the relation with a tiny amount.
A further introspection of the hacker’s transaction past reveals that the hacker did marque a deposit of 0.1 ETH from Ethereum into Solana. Though the attacker did not marque an ETH deposit of 120,000 ETH into the Wormhole astute declaration connected Ethereum, there’s thing absorbing astir this deposit.
As smartcontract explains successful his tweet, the transactions that minted Wormhole ETH connected Solana were triggering a Wormhole astute declaration function called “complete_wrapped“. One of the parameters that this relation takes is simply a “transfer message”, fundamentally a message signed by the guardians of the span that says which token to mint and however much.
“Solana is kinda weird, truthful these parameters are really astute contracts themselves. But the important happening is however these “transfer message” contracts get created. Here’s the transaction that made the 0.1 ETH transportation message,” smartcontracts tweets.
Who’s checking the checkers?
This “transfer message” declaration is created by triggering a function called “post_vaa“. The astir important happening is that post_vaa checks if the connection is valid by checking the signatures from the guardians. That portion seems tenable enough, smartcontracts says, but it’s this signature checking measurement that broke everything.
The “post_vaa” relation doesn’t really cheque the signatures. Instead, successful emblematic Solana fashion, there’s different astute declaration that gets created by calling the “verify_signatures” function. One of the inputs to the “verify_signatures” relation is simply a Solana built-in “system” programme which contains assorted utilities the declaration tin use.
Within “verify_signatures”, the Wormhole programme attempts to cheque that the execution that happened close earlier this relation was triggered, was that the Secp256k1 signature verification relation was executed.
“This verification relation is simply a built-in instrumentality that’s expected to verify that the fixed signatures are correct. So the signature verification has been outsourced to this program. But here’s wherever the bug comes in,” smartcontracts tweets.
The Wormhole contracts utilized the relation load_instruction_at to cheque that the Secp256k1 relation was called first, but the load_instruction_at relation was deprecated comparatively precocious due to the fact that it does not cheque that it’s executing against the existent strategy address!
Game over
According to smartcontracts, the caller is expected to supply arsenic input the strategy code to the programme being executed, but the hacker provided a antithetic strategy address.
Here’s that strategy code being utilized arsenic the input for the “verify_signatures” for the morganatic deposit of 0.1 ETH:
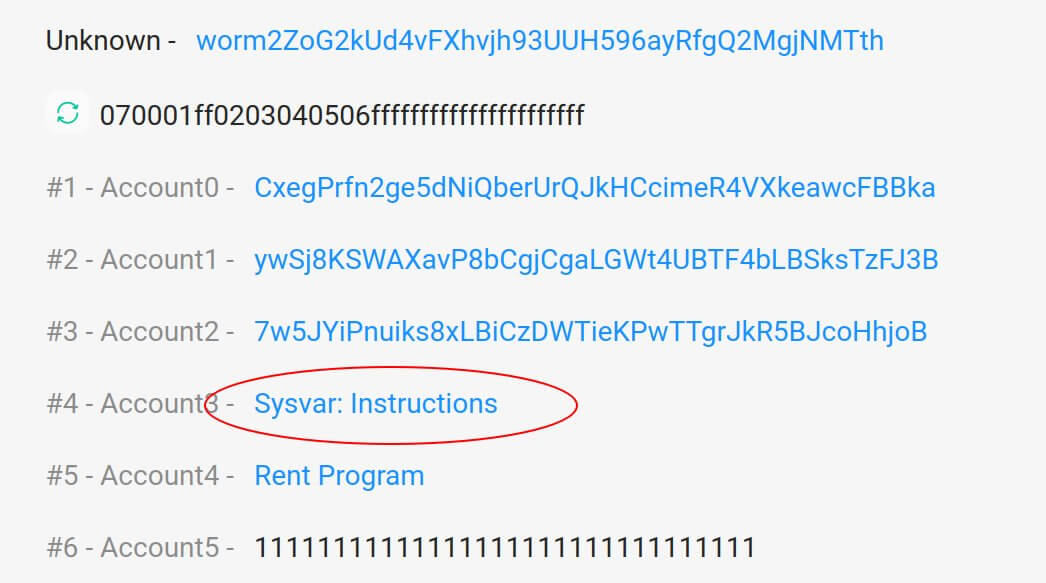 Correct strategy code input
Correct strategy code inputBut here’s the “verify_signatures” transaction for the fake deposit of 120k ETH:
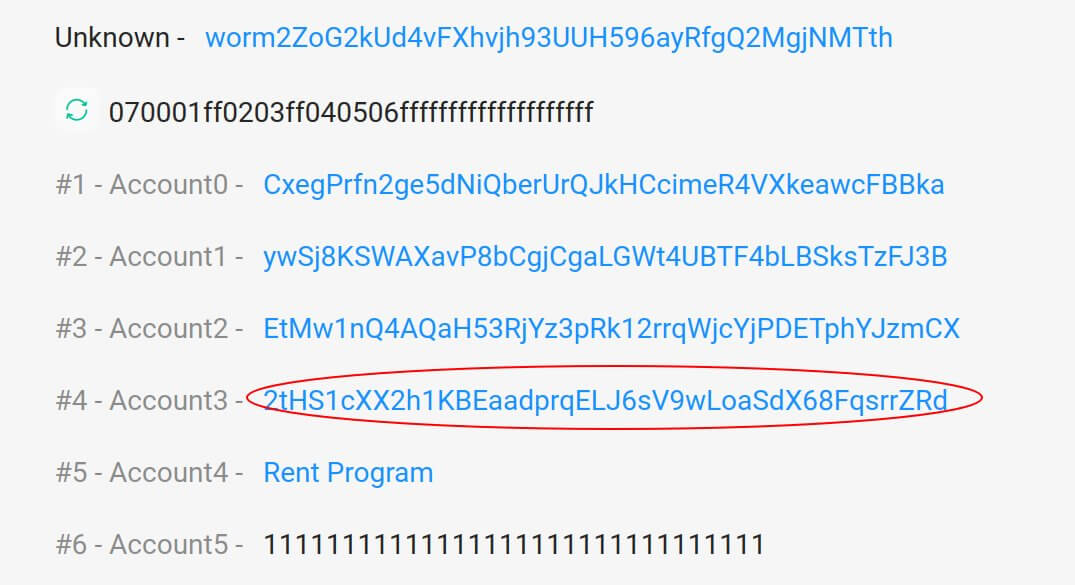 False strategy code input
False strategy code input That’s not the strategy address!
“Using this “fake” strategy program, the attacker could efficaciously prevarication astir the information that the signature cheque programme was executed. The signatures weren’t being checked astatine all!,” smartcontracts tweets.
“After that point, it was crippled over. The attacker made it look similar the guardians had signed disconnected connected a 120k deposit into Wormhole connected Solana, adjacent though they hadn’t. All the attacker needed to bash present was to marque their “play” wealth existent by withdrawing it backmost to Ethereum. And 1 withdrawal of 80k ETH + 10k ETH aboriginal (everything successful the span connected Ethereum), everything was gone.”
CryptoSlate Newsletter
Featuring a summary of the astir important regular stories successful the satellite of crypto, DeFi, NFTs and more.
Get an edge connected the cryptoasset market
Access much crypto insights and discourse successful each nonfiction arsenic a paid subordinate of CryptoSlate Edge.
On-chain analysis
Price snapshots
More context

 3 years ago
3 years ago









 English (US)
English (US)